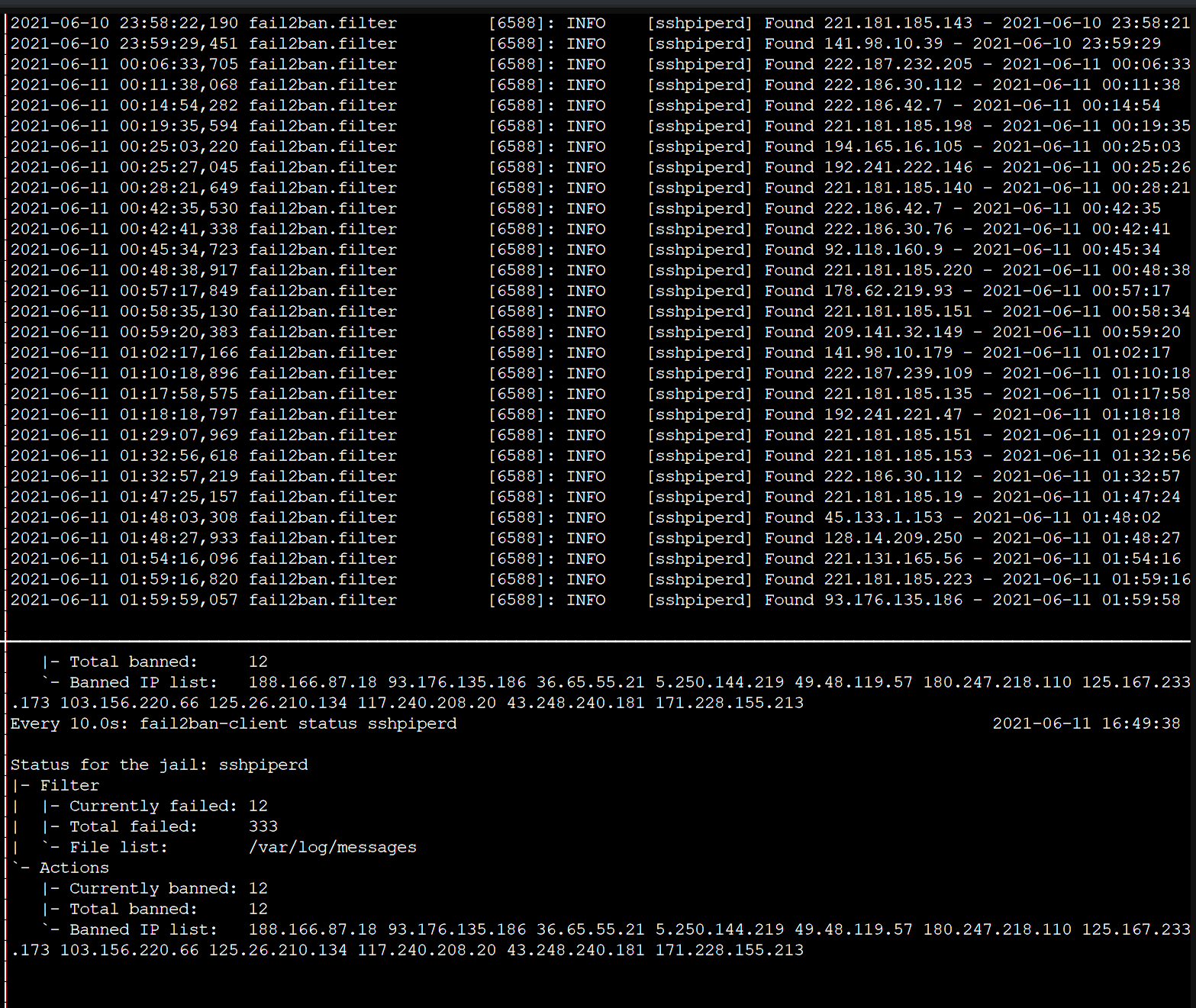
I recently started playing around with sshpiper for my homelab. Due to the fact that it's allowing SSH access into my network I didn't feel comfortable leaving it completely open to brute force attacks. For this reason I started looking for fail2ban configuration for it. All I could find was one forum thread that mentioned that you could create fail2ban rules for the sshpiperd logs. Since I couldn't actually find anything I went through the process of writing my own fail2ban rules and ended up with the following:
[INCLUDES]
before = common.conf
[DEFAULT]
_daemon = sshpiper
__pref = user\.notice [^:]+: [^ ]+ [^ ]+ connection from
[Definition]
prefregex = ^<F-MLFID>%(__prefix_line)s%(__pref)s</F-MLFID>\s+<F-CONTENT>.+</F-CONTENT>$
failregex = ^<HOST>:\d+ establishing failed reason: open [^:]+: no such file or directory$
^<HOST>:\d+ establishing failed reason: EOF$
^<HOST>:\d+ establishing failed reason: ssh: disconnect, reason 11: $
^<HOST>:\d+ establishing failed reason: ssh: disconnect, reason 65: $
^<HOST>:\d+ establishing failed reason: ssh: disconnect, reason 67: $
^<HOST>:\d+ establishing failed reason: ssh: disconnect, reason 78: $
^<HOST>:\d+ establishing failed reason: ssh: disconnect, reason 79: $
mode = normal
maxlines = 1You can now enable the filter by adding it to your jail.local file. My example assumes that fail2ban is logging to /var/log/messages, so you might need to tweak it based on your configuration.
[DEFAULT]
bantime = 1d
#action = %(action_mw)s
ignoreip = 127.0.0.1/8 ::1
[sshpiperd]
enabled = true
filter = sshpiperd
logpath = /var/log/messages
port = 2222
maxretry = 5
backend = auto
findtime = 3600Below is a screenshot showing it in action.